Index >> Network & Internet >> Servers >> Intrusion Detection and Defense System
Report SpywareIntrusion Detection and Defense System 2.1.0
Software Description:
Intrusion Detection and Defense System - IDDS defends your Windows servers against brute force attacks
Cyberarms IDDS enhances Security by denying access to intruders on the network level
Cyberarms provides a pro-active Intrusion Detection and Defense System (IDDS). It's pro-active, because it not only logs, but also reacts to intrusion attempts.
Once a "bad guy" is recognized, he won't have access to any of your systems protected by Cyberarms IDDS. Don't give a second chance to hackers!
High performance, extremely small footprint and ultra low system overhead
Additional software almost always implies additional risk. But not with Cyberarms Security Systems, as the existing system functionality of Windows is re-used.
Our software uses the Windows event log for security analysis and intrusion detection (among other sources), and it configures the Windows firewall to dynamically deny access to hackers on a very low system level.
Configure and adapt your Security System to meet 100 % your needs
Cyberarms IDDS covers the most common use-cases out of the box. In addition you can protect your own applications and cover almost any use-case with the powerful configuration-tool or the extendible API.
Full control - whitelist trusted networks and determine how and in which case your IDDS shall react
Adapt the default settings in order to determine which kind of intrusion attempts you want to focus on and what consequences shall be taken when suspicious behavior occurs. Whitelist trusted networks to never deny access to clients from these networks. Get notified about every recognized attempt to attack your systems and the action taken.
What's New: Completely redesigned user interface with Intrusion Detection statistics, scheduled reports for the Professional edition
Limitations: The FREE edition defends against up to five attacks per day - sufficient for most systems
Cyberarms IDDS enhances Security by denying access to intruders on the network level
Cyberarms provides a pro-active Intrusion Detection and Defense System (IDDS). It's pro-active, because it not only logs, but also reacts to intrusion attempts.
Once a "bad guy" is recognized, he won't have access to any of your systems protected by Cyberarms IDDS. Don't give a second chance to hackers!
High performance, extremely small footprint and ultra low system overhead
Additional software almost always implies additional risk. But not with Cyberarms Security Systems, as the existing system functionality of Windows is re-used.
Our software uses the Windows event log for security analysis and intrusion detection (among other sources), and it configures the Windows firewall to dynamically deny access to hackers on a very low system level.
Configure and adapt your Security System to meet 100 % your needs
Cyberarms IDDS covers the most common use-cases out of the box. In addition you can protect your own applications and cover almost any use-case with the powerful configuration-tool or the extendible API.
Full control - whitelist trusted networks and determine how and in which case your IDDS shall react
Adapt the default settings in order to determine which kind of intrusion attempts you want to focus on and what consequences shall be taken when suspicious behavior occurs. Whitelist trusted networks to never deny access to clients from these networks. Get notified about every recognized attempt to attack your systems and the action taken.
What's New: Completely redesigned user interface with Intrusion Detection statistics, scheduled reports for the Professional edition
Limitations: The FREE edition defends against up to five attacks per day - sufficient for most systems
100% Clean:
 Intrusion Detection and Defense System 2.1.0 is 100% clean
Intrusion Detection and Defense System 2.1.0 is 100% cleanThis download was tested thoroughly and was found 100% clean. Click "Report Spyware" link on the top if you found this software contains any form of malware, including but not limited to: spyware, viruses, trojans and backdoors.
Related Software:
- Service - O - Matic 3.00 - Run any windows application as a windows service
- Axigen Business Messaging for Linux 8.0 - Axigen - Business Mail Server, Calendaring & Collaboration with 24x7 support
- Cyclope Internet Filtering Proxy 4.0 build 300 - Cyclope Internet Filtering Proxy is an Internet Filtering Software
- Simple DNS Plus 5.2 - The simple yet powerful DNS server for Windows
- Courier Mail Server 3.01 - Courier Mail Server is a e-mail server. Contains Web and SOCKS servers.
- AceFTP 3 Pro 3.72.0 - AceFTP 3 Pro is about total control, security, efficiency, and simplicity.
- AXIGEN Gateway Mail Server 1.2.5 - AXIGEN Gateway- secure mail relay server with FREE support
- Free SMTP Server 2.5994 - Free SMTP Server is a local SMTP server program for Windows
- SMTP Server Pro 5.27 - Easy-to-use SMTP POP3 mail server program designed for high-volume messaging.
- DWebPro 8.4.4 - DWebPro is a stand-alone web-server with CGI, PHP/MySQL, SMTP Server on CD.
top 10 most downloaded
recommended software
-
- Gear Software Manager
- Gear Software Manager is a free software version online check software. First, Gear Software Manager scans versions of all software installed in your...
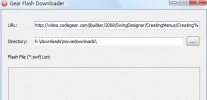
-
- Gear Flash Downloader
- Gear Flash Downloader is a free handy tool to download SWF Flash files from web pages. Gear Flash Downloader is very easy to use. Simply copy and past...